Testing
Penetration Tests
Testing the effectiveness and resilience of your security mechanisms from the perspective of an external attacker (hacker). Testing is usually done by simulating an attack on a network infrastructure, a part of it (e.g. Wi-Fi network), or a specific application (web or mobile). The output is a clear final report listing the vulnerabilities found, assessing their severity and proposing appropriate countermeasures.

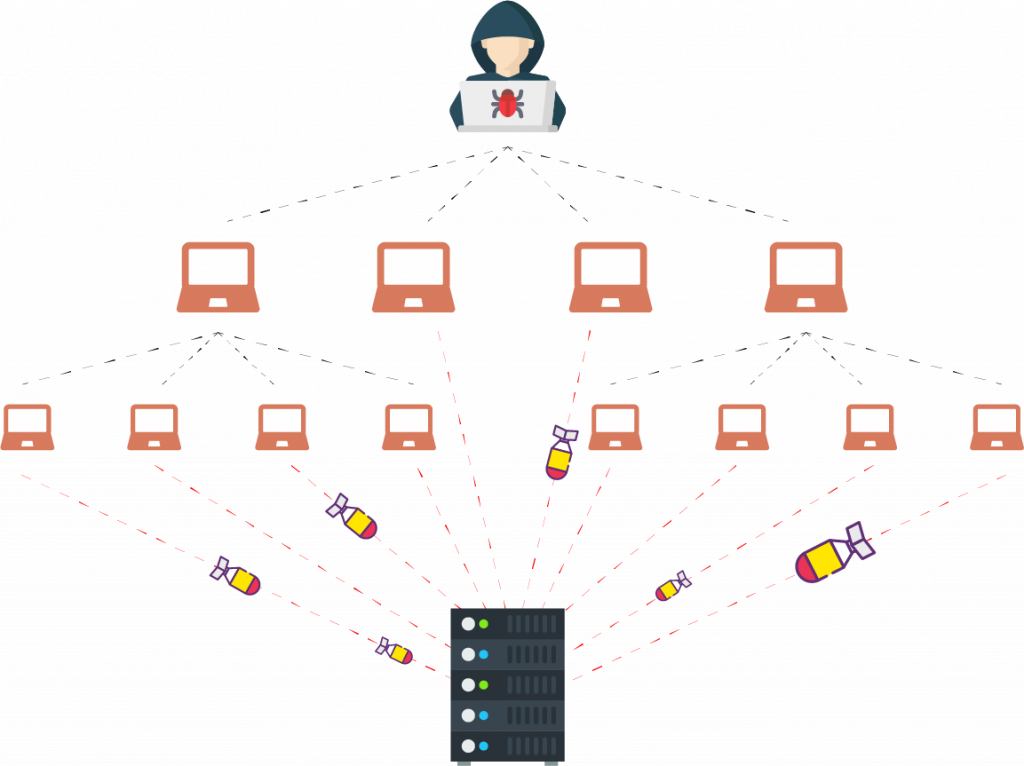
Stress and (D)DoS Tests
Testing your system's response to several types of (D)DoS attacks designed to make the system or part of it (e.g. a web application) inaccessible to users. The system responses are shown in a graph in the final report. The report includes a discussion of possible countermeasures.

Social Engineering
Examine your system users' practices using social engineering methods (e.g. e-mail and voice phishing). The goal is to determine the likelihood that sensitive information (e.g. login credentials, personal information, or trade secrets) could be leaked this way. The output is a final report and user training.