Consultation
Current Situation Analysis
The state-of-the-art analysis provides an overview of the cyber security from the chosen point of view (e.g. network architecture, malware protection, user and role management, physical security...). Subsequently, potentially problematic areas are predicted and possible steps towards their elimination are suggested. The document is the basis for most of the consulting and implementation activities.

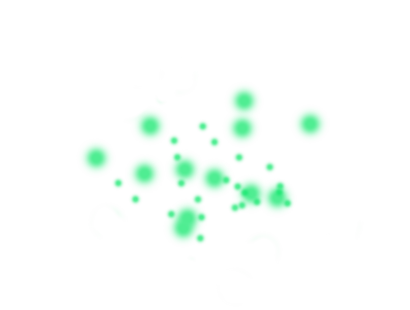
Risk Analysis
Risk analysis is a comprehensive and in-depth analysis of the current situation. The primary objective is to identify all hardware, software and information(usually the most valuable!) assets, evaluate them, list their vulnerabilities, list possible threats, estimate the probability of their occurrence and propose effective and available solutions to eliminate them. This is a key document for security and risk management processes.
Security Documentation
Development of basic and extended documentation for safety and risk management processes. This includes, for example, a security policy, a user or administrator manual, a backup and recovery plan, etc. These documents are based on the conclusions of previous analysis, the results of tests and audits, or the company's internal plans and strategies. They are used in daily practice as binding documents according to which security and risk management processes are maintained in accordance with defined needs and objectives.

Physical Security
Comprehensive assessment of the security of hardware assets against physical damage or theft. Risk factors include, for example, inappropriate temperature (cooling system, air conditioning, fire protection system), unauthorized access (access and camera system), contact with water, etc. The final report lists the risks and proposes appropriate measuresto eliminate them.

Security Incident Response
Forensic analysis of available information (e.g. logs, CCTV footage, etc.) to confirm or refute the suspected existence of a security incident. Design and implementation of security measures to protect the system from similar incidents, repair damage (e.g. restoration from backups), or detect the perpetrator.